
Exploring Cybersecurity Services In The USA & Canada: Protect Your Online Data
The Insider Threat: The Trojan Horse Within
It’s said “keep your friends close, but your enemies closer,” an adage that rings true in the world of cybersecurity. Insider threats often go undetected until it’s too late, as these attackers already have some level of trust within the organization — a devastating Trojan horse situation.
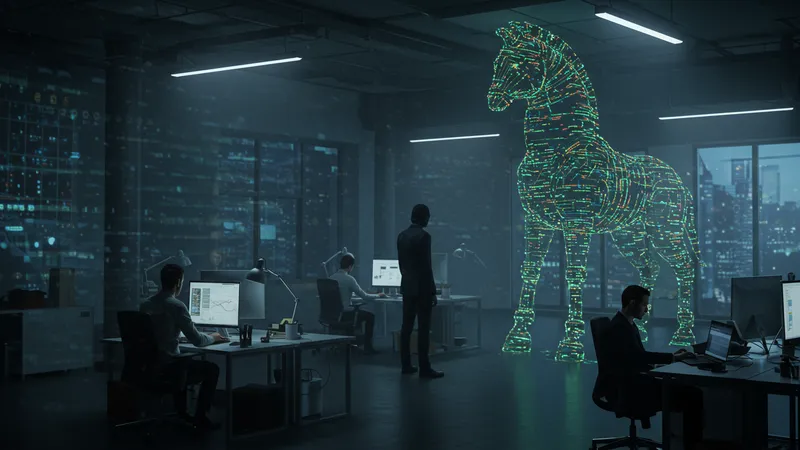
Whether it’s a disgruntled employee seeking revenge or an unintentional action leading to a breach, the damage can be catastrophic. Surprisingly, these insiders were responsible for 34% of all data breaches, a statistic that goes largely unreported in mainstream discussions.
Solutions for detecting and mitigating insider threats include monitoring software that flags unusual activity, but such measures ignite debates about privacy vs. security. How companies navigate these waters is make-or-break for trust internally and externally.
As organizations evolve, so do the access points for threats from within. But there’s more than just digital treachery to consider — an emerging risk on the horizon changes everything we know about insider threats. Don’t blink now.